Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release
Organizations need to protect their data assets from external and internal threats, and there are numerous strategies and protocols available to help achieve this goal. One of the most effective methods of providing robust security throughout an IT environment is the Zero Trust model.
This post will look at the details of the Zero Trust model, the necessary steps to implement Zero Trust, and how data loss prevention (DLP) software can be an important component of a Zero Trust environment.
In this article:

The Zero Trust model is an approach to IT security that requires all users to be continuously authorized and authenticated before being granted access to systems, applications, or data resources. The name Zero Trust aptly defines the underlying focus of the model, which is to trust no individual or entity regarding access to the IT environment. By default, nothing is trusted in a Zero Trust architecture.
Traditional security frameworks assume that once an individual gains access to the network, they should be trusted throughout the infrastructure. This mindset has proven risky as threat actors who successfully subvert network security can run rampant throughout the environment.
In addition to this problem, it can be extremely difficult to address insider threats with legacy security models.
Zero Trust security eliminates the concept of a traditional network edge. Modern networks are complex architectures constructed with a combination of on-premises and cloud resources. They are accessed by employees from virtually any location, complicating the process of securing valuable company resources.
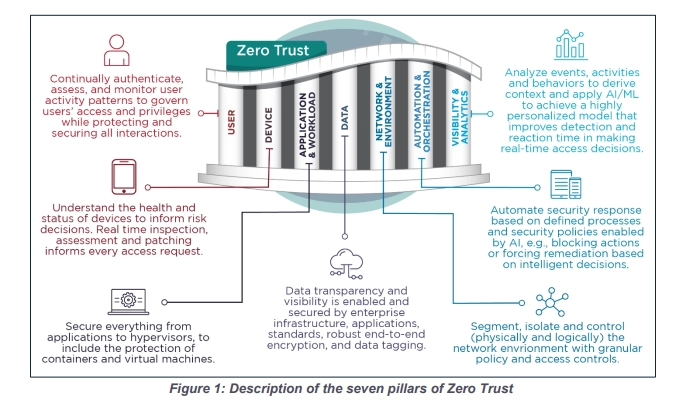
Zero Trust is based on seven pillars. These fundamental principles are designed to enhance security by assuming that threats can exist both inside and outside a network.
It's important for organizations to understand these core components of Zero Trust to ensure a successful implementation. Here's a brief summary of the seven Zero Trust pillars.

Implementing Zero Trust presents several challenges for organizations. Complex infrastructure and legacy system dependencies can hinder smooth adoption. Gaining buy-in from stakeholders across departments is crucial but often difficult.
When planning implementation, key considerations include ease of deployment, scalability to accommodate future growth, and robust security measures to protect against evolving threats.
The time required for full implementation varies significantly depending on organizational size, existing infrastructure, and resource allocation.
Organizations must carefully assess their current environment, identify critical assets and access points, and develop a phased approach to minimize disruption. Continuous monitoring and adjustment of policies are essential for maintaining an effective Zero Trust model as the threat landscape evolves.

Implementing the Zero Trust security model requires the following steps to protect all IT resources regardless of their location.
All assets should be identified and classified based on sensitivity and organizational value. This includes networks, devices, applications, and data resources. A complete picture of IT resources is necessary to protect them effectively.
A solution like the Reveal Platform by Next automates this process with lightweight, next-gen endpoint agents driven by machine learning to identify and categorize data at the point of risk, as it enters the environment.
The most efficient method of implementing Zero Trust is to start with a core team, which will be responsible for planning and implementing the Zero Trust processes and procedures.
In order to ensure a successful implementation, the team should include members of the following three key areas within the IT environment:
These specific security areas will be used together to implement Zero Trust. Additional team members should be drafted from security operations and risk management.
A comprehensive policy needs to be created that defines the goals and guidelines for Zero Trust across the environment, with strict access controls and continuous verification forming essential components of this policy.
The details of the policy regarding data access should be replicated in a company’s data handling policy which is used by a DLP solution to protect resources.
The ultimate goal is to provide comprehensive security across the organization. The most effective method of implementing this security is by focusing on one of the three key aspects discussed when developing the team and the specific protective measures they offer.
Once the first area has been secured, the other two should also be implemented to enforce the Zero Trust policy.
Select and implement security solutions and best practices such as the principle of least privilege to limit data access and strong encryption to protect valuable assets. Monitor and log all user activity to identify suspicious behavior.
Users should be trained on newly introduced technology to better understand how they contribute to protecting company resources.
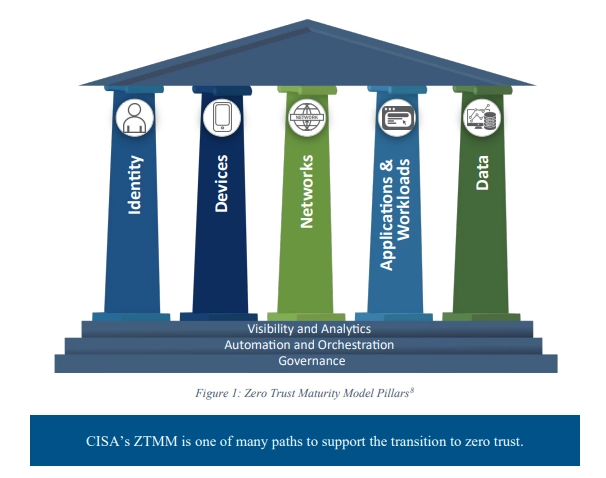
When choosing an implementation focus and subsequently implementing the other components of Zero Trust architecture, it's helpful to refer to a Zero Trust roadmap like the Zero Trust Maturity Model.
The Zero Trust Maturity Model (ZTMM) is a framework developed by the Cybersecurity & Infrastructure Security Agency (CISA) that organizations use to assess their current security posture and guide the implementation of Zero Trust principles. It helps organizations to systematically adopt Zero Trust strategies and measures, improving their security resilience over time.
The model typically includes several stages or levels of maturity, each representing a different degree of implementation and integration of Zero Trust principles. The Zero Trust Maturity Model is based on five pillars and three cross-cutting capabilities.
The five pillars in the Zero Trust Maturity Model include:
Each of these pillars includes details related to the three cross-cutting capabilities, which include:
Within each pillar, there are also examples of Zero Trust architectures in the various phases of Zero Trust maturity, including:
Organizations should aim to progress to the Advanced and Optimal levels of maturity over time.
A data loss prevention solution such as the Reveal Platform by Next supports Zero Trust by enforcing an organization’s data handling policy. The platform continuously monitors user activity and prohibits the deliberate or accidental misuse of sensitive and valuable data resources.
Reveal also offers instructive incident-based user training at the point of risk as it prevents information from being misused.
Talk to the experts at Next and book a demo to see Reveal in action. See for yourself how this modern and powerful DLP platform supports Zero Trust and protects your valuable data.
Zero Trust protects an IT environment from insider threats by never trusting any activity initiated by an entity unless it can be authenticated. Insiders typically have access to a subset of IT resources necessary to perform their jobs.
A Zero Trust approach requires users to continuously authenticate and will restrict access to resources they are not authorized to use.
Device security is essential in a Zero Trust environment to ensure unauthorized users have not compromised a device to gain access to the IT infrastructure. Threat actors can leverage a lost or stolen device to access restricted resources.
Practices such as multi-factor authentication safeguard organizations against this issue. Unauthorized users will not be able to receive the secondary authentication necessary to perform a given activity.
An organization should select a Zero Trust implementation focus based on an evaluation of existing security measures. The decision to begin implementing Zero Trust should address the nature of the business and the type of data resources that are being protected. User and device security is often a good place to start to control remote access to cloud resources.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources

